How AWS Organizations Tag Policies Strengthen Cost Management and Access Governance
Managing a large amount of cloud resources at scale often brings one recurring challenge - tag inconsistency. Whether it’s for cost allocation, automation or access control, having well-structured and standardized tags is essential. However, in large multi-account environments, enforcing consistent tagging across teams and workloads can quickly become complex. AWS Organizations tag policies help you define and maintain a framework for tag consistency across your environment, giving you visibility and control over your resources.
In this post, we explore how tag policies work, how they integrate with AWS Organizations and how you can combine them with other AWS services to automate compliance, improve cost visibility and strengthen governance.
Establishing Consistency with AWS Tag Policies
AWS tag policies allow you to define a centralized set of rules that describe how tags should be structured across your organization. These rules can define tag keys, enforce case sensitivity and restrict tag values to specific allowed options. For example, you might require the Environment tag to only use values such as Prod, Dev or Test, or ensure that all tag keys are consistently cased. Tag policies are defined and managed through the management account in AWS Organizations and can be attached to organizational units (OUs) or individual member accounts. Once applied, AWS evaluates your resources against these policies and determines whether the tags are compliant or noncompliant with the effective policy [1].
The following tag policy set demonstrates a best-practice approach according to AWS to establish consistent tagging standards across an AWS Organization [2]. The root-level policy defines the approved tag keys: Environment and OwnerTeam and enforces their exact case. By attaching this policy to the organization’s root OU, all member accounts inherit these standardized tag keys. The @@operators_allowed_for_child_policies parameter is set to ["@@none"], ensuring that no lower-level tag policies can override the tag key definitions or alter their case sensitivity. This promotes consistent naming conventions throughout the organization. The OU-level policy builds on the foundation set by the root policy by defining the acceptable tag values for each key. For example, resources can only use Prod, Test or Dev for the Environment tag and the OwnerTeam tag can only include Platform, Analytics or Security. This approach helps maintain uniform tagging practices, which are essential for reliable cost allocation, operational automation and access control.
The root OU’s tag policy could be defined as:
{
"tags": {
"Environment": {
"tag_key": {
"@@assign": "Environment",
"@@operators_allowed_for_child_policies": ["@@none"]
}
},
"OwnerTeam": {
"tag_key": {
"@@assign": "OwnerTeam",
"@@operators_allowed_for_child_policies": ["@@none"]
}
}
}
}
A child OU’s tag policy could be defined as:
{
"tags": {
"Environment": {
"tag_value": {
"@@assign": [
"Prod",
"Test",
"Dev"
]
}
},
"OwnerTeam": {
"tag_value": {
"@@assign": [
"Platform",
"Analytics",
"Security"
]
}
}
}
}
It’s important to note that tag policies are not enforced by default. You can still create resources with noncompliant tags unless enforcement is explicitly enabled. However, when enforcement is turned on, AWS prevents the creation or modification of resources with tags that do not comply with the policy in place [1].
Additionally, untagged resources or tags not defined in the policy are not evaluated for compliance. To ensure critical resources are always tagged, you can use service control policies (SCPs) at the OU or account level to deny resource creation when required tags are missing. The following SCP prevents IAM users and roles in affected accounts from creating new Amazon S3 buckets unless the Environment tag is included in the request. Following the previous example on setting up the tag policy, the Environment tag could be used to distinguish between Prod, Dev and Test environments. By attaching this SCP to an OU or an account, you ensure that all newly created S3 buckets are tagged at creation time, helping maintain consistent metadata for governance and cost allocation. When combined with a tag policy that enforces consistent and compliant Environment tag values for S3 buckets, this approach ensures that every newly created bucket is both properly tagged and aligned with your organization’s tagging standards.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "DenyCreateS3BucketWithoutEnvironmentTag",
"Effect": "Deny",
"Action": "s3:CreateBucket",
"Resource": "*",
"Condition": {
"Null": {
"aws:RequestTag/Environment": "true"
}
}
}
]
}
It is important to mention that although this policy follows AWS best practices for tagging enforcement, it should be tested carefully in your environment before a wider deployment throughout your organization. Similar to other deny-based policies, it may affect service operations that perform resource creation in multiple steps. For example, AWS CloudFormation creates some resources before applying tags and an SCP like this would prevent such stacks from being deployed successfully [3]. To avoid interruptions, consider testing in a non-production environment and modifying the SCP policy to best fit your needs and use case.
Gaining Organization-Wide Visibility into Tag Compliance
Tag policies integrate with the AWS Resource Groups Tagging API, allowing you to generate organization-wide reports on tag compliance [4]. With this capability, you can quickly identify which resources are aligned with your tagging standards and which are not. You can view this data not only at the organization-level but also at the individual account-level [5], giving you a comprehensive view of your tagging posture.
To monitor compliance in near real-time, tag policy evaluation events are also integrated with Amazon EventBridge. Whenever a noncompliant tag is created, an event is emitted. You can use this event to trigger automation: for example, automatically updating or removing noncompliant tags using the TagResources and UntagResources operations in the Resource Groups Tagging API [6]. For organizations that prefer a more centralized governance model, these EventBridge events can be routed from member accounts to a central event bus in a dedicated administrator account. From there, you can aggregate alerts, send notifications to a centralized Amazon SNS topic or trigger further automation across the organization.
In addition to near-real-time monitoring, you can also enforce tag compliance on a scheduled basis using AWS Config. With custom Config rules, you can periodically evaluate resources, such as once per day, and automatically remediate noncompliant tags. At scale, you can deploy these rules using AWS Config conformance packs through a delegated administrator account. This approach provides a consistent, automated framework for managing and auditing tagging standards across all accounts in your organization.
Enabling Cost Control and Visibility
Consistent tagging is a fundamental component of effective cost management in AWS. When your tags follow predictable structures and naming conventions, services such as AWS Cost Explorer, AWS Budgets and AWS Cost and Usage Reports become far more insightful and useful. With standardized tags, you can easily break down and analyze costs by environment, owner team, project or business unit, ensuring that spending is accurately attributed to the right cost centers. This visibility enables finance and operations teams to forecast budgets with greater confidence.
Tag policies play a key role in maintaining this consistency automatically. By defining approved tag keys and permissible values, you can prevent errors such as inconsistent capitalization, misspellings or ad-hoc naming that often cause inaccurate and fragmented reporting. Over time, this leads to a cleaner and a lot more trustworthy cost dataset, allowing you to make informed decisions about resource usage optimizations.
Beyond allocation, consistent tagging also drives proactive cost optimization. For instance, you can use tags to identify resources that are underutilized or no longer needed, such as unused development instances or idle storage buckets, and automate their cleanup. Similarly, tags can power automated budget alerts and dashboards that highlight overspending within a specific project or team.
Improving tagging standards allows organizations to gain a complete picture of their cloud footprint, uncover hidden or unmanaged spend and establish transparent cost ownership across departments. When paired with governance mechanisms such as AWS Organizations tag policies and SCPs that enforce tag presence, these practices create a strong foundation for sustainable cloud financial management and operational excellence.
Strengthening Access Control with Attribute-Based Access Control (ABAC)
AWS tagging and tag policies are not only useful for cost tracking and governance - they also play a critical role in enabling attribute-based access control (ABAC). ABAC is an advanced authorization model where access permissions are granted dynamically based on user attributes and resource tags. Instead of maintaining long lists of static permissions, you define policies that allow access only when the user’s attributes match the tags on a resource. This approach brings flexibility and scalability to identity and access management across large organizations.
Consider a company that uses AWS IAM Identity Center integrated with Okta as its external identity provider. Through the System for Cross-domain Identity Management (SCIM) protocol, Okta groups such as Engineers, DataScience or CyberSecurity are automatically synchronized with AWS Identity Center groups. Along with group membership, Okta can also pass user attributes such as environment, project or team. These attributes are injected as session tags when a user signs in to AWS and assumes a role [7]. With ABAC, you can design permission sets that use these session tags to control access dynamically. For example, a user whose session includes the tag Project=Analytics will only be able to interact with AWS resources (like Amazon S3 buckets or Amazon EC2 instances) that are tagged with the same Project=Analytics key-value pair. Similarly, developers working in the Environment=Test context can be limited to resources tagged as part of the staging environment, ensuring that no unintended changes occur in production systems. The alignment between user identity and resource metadata allows access to scale automatically as teams and projects change without needing to manually update IAM policies for each user or resource.
However, the effectiveness of ABAC depends entirely on consistent and accurate tagging. If tags are misspelled, use inconsistent capitalization or deviate from approved naming conventions, access controls can fail silently - either blocking legitimate users or allowing unintended access. This is where AWS Organizations tag policies become essential. As previously mentioned, tag policies define the exact structure, casing and permissible values for tag keys used across your environment. When enforced, they ensure that both resources and session tags follow the same standard.
Combining ABAC with tag policies, organizations can establish a reliable, automated security framework that ensures access is granted predictably - according to defined governance standards. Teams can manage permissions at scale and ensure that identity-driven access remains consistent with organizational policies.
The following diagram represents an architecture of a multi-account environment in AWS Organizations that has been integrated with AWS IAM Identity Center (with external IdP), ABAC permission sets and tag policies:
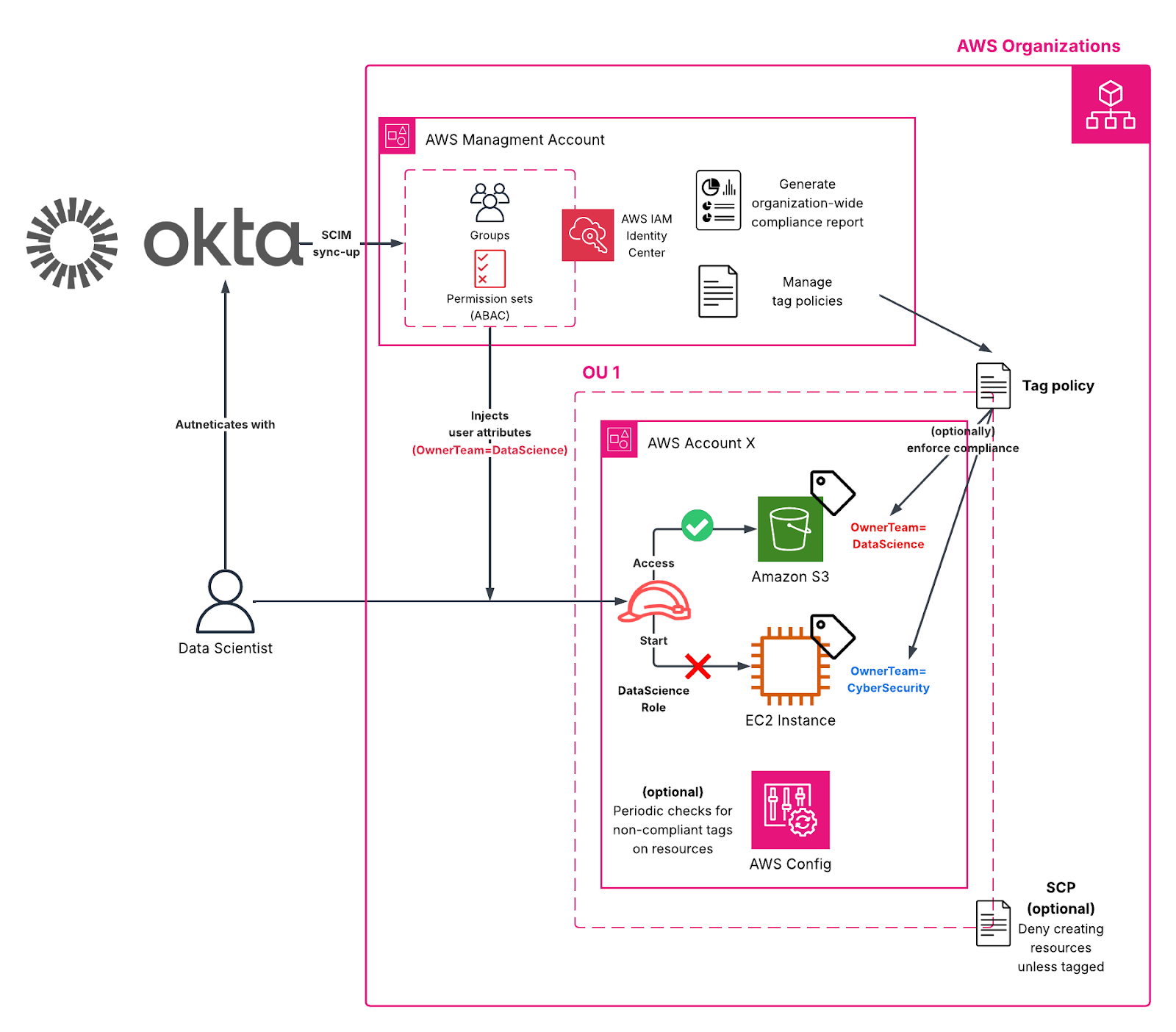
What This Means for You
Standardizing your tagging strategy with AWS Organizations tag policies can have an immediate and measurable impact on your AWS environment. Consistent tagging gives you the foundation for clear visibility into how resources are used, who owns them and how much they cost. When every resource follows the same tagging structure, you can easily track spending by project, department or environment and identify unused or underutilized assets. This level of insight helps teams make smarter budgeting decisions and ensures that financial accountability is shared across your organization. If your organization uses AWS Identity Center and/or integrates with an external identity provider and relies on tags to determine permissions through ABAC, implementing tag policies becomes even more critical. Tag policies ensure that tags are applied consistently and follow predictable patterns, so permissions based on those tags behave as intended. This reduces the chance of unexpected access issues and ensures that users can only interact with the resources aligned to their roles or projects. Standardizing your tagging framework helps you build a more reliable and well-governed cloud environment which supports both cost control and secure, scalable access management.
What’s Next
If you find this approach to tagging and governance valuable, our team at Several Clouds can help you explore how these concepts fit within your own AWS environment. Every organization has unique structures, compliance requirements and operational goals, and implementing tag policies can look different depending on those factors. Our AWS experts can work with you to design and integrate a tagging strategy that aligns with your business needs, ensuring your tagging framework supports your cost management, security and scalability objectives. If you’re ready to see how this architecture can be adapted to your specific use cases, reach out to our team to start the conversation.
📅 Whether it’s GenAI, CI/CD, or cloud cost chaos — we’ve seen it before.
Let’s walk through how we’ve solved it, and see if it fits your world.
References
[1] “Tag policies”, AWS Docs, https://docs.aws.amazon.com/organizations/latest/userguide/orgs_manage_policies_tag-policies.html
[2] “Tag policy syntax and examples”, AWS Docs, https://docs.aws.amazon.com/organizations/latest/userguide/orgs_manage_policies_example-tag-policies.html
[3] “Example SCPs for tagging resources”, AWS Docs,
[4] “Generating an organization-wide compliance report with AWS Organizations”, AWS Docs,
https://docs.aws.amazon.com/organizations/latest/userguide/enforcement-report.html
[5] “Finding non-compliant resources for an account with AWS Organizations”, AWS Docs,
https://docs.aws.amazon.com/organizations/latest/userguide/enforcement-finding.html
[6] “Correcting non-compliant tags in resources with AWS Organizations”, AWS Docs,
https://docs.aws.amazon.com/organizations/latest/userguide/enforcement-correcting.html
[7] “Multi-Account Multi-Region Data Aggregation for AWS Config”, AWS Docs,
https://docs.aws.amazon.com/config/latest/developerguide/aggregate-data.html
[8] “Attributes for access control”, AWS Docs,
https://docs.aws.amazon.com/singlesignon/latest/userguide/attributesforaccesscontrol.html
Relevant Success Stories
Book a meeting
Ready to unlock more value from your cloud? Whether you're exploring a migration, optimizing costs, or building with AI—we're here to help. Book a free consultation with our team and let's find the right solution for your goals.

.png)

.png)